Mastering SSH Remote IoT Device Management: The Ultimate Guide
SSH remote IoT device management has become an essential skill for modern tech enthusiasts and professionals alike. With the rapid growth of interconnected devices, understanding Secure Shell (SSH) and its applications in remote management is no longer optional. This article will take you through everything you need to know about securely managing IoT devices remotely using SSH, ensuring your network remains protected while maintaining optimal performance.
As the Internet of Things (IoT) continues to expand, the demand for secure and efficient remote management solutions has skyrocketed. SSH offers a robust and reliable way to control and monitor IoT devices from anywhere in the world. Whether you're a beginner or an advanced user, this guide will walk you through the basics, advanced techniques, and best practices for SSH remote IoT device management.
This article is designed to provide comprehensive insights into SSH remote IoT device management, covering everything from setting up secure connections to troubleshooting common issues. By the end of this guide, you'll have the knowledge and tools necessary to confidently manage your IoT devices remotely.
Read also:Mastering Remoteiot Vpc Ssh Raspberry Pi A Free Windows Download Guide
Table of Contents
- Introduction to SSH Remote IoT Device Management
- What is SSH?
- Benefits of Using SSH for IoT Devices
- Setting Up SSH for IoT Devices
- Securing Your SSH Connections
- Managing IoT Devices Remotely with SSH
- Troubleshooting Common SSH Issues
- Best Practices for SSH Remote IoT Device Management
- Applications of SSH in IoT
- The Future of SSH in IoT
- Conclusion
Introduction to SSH Remote IoT Device Management
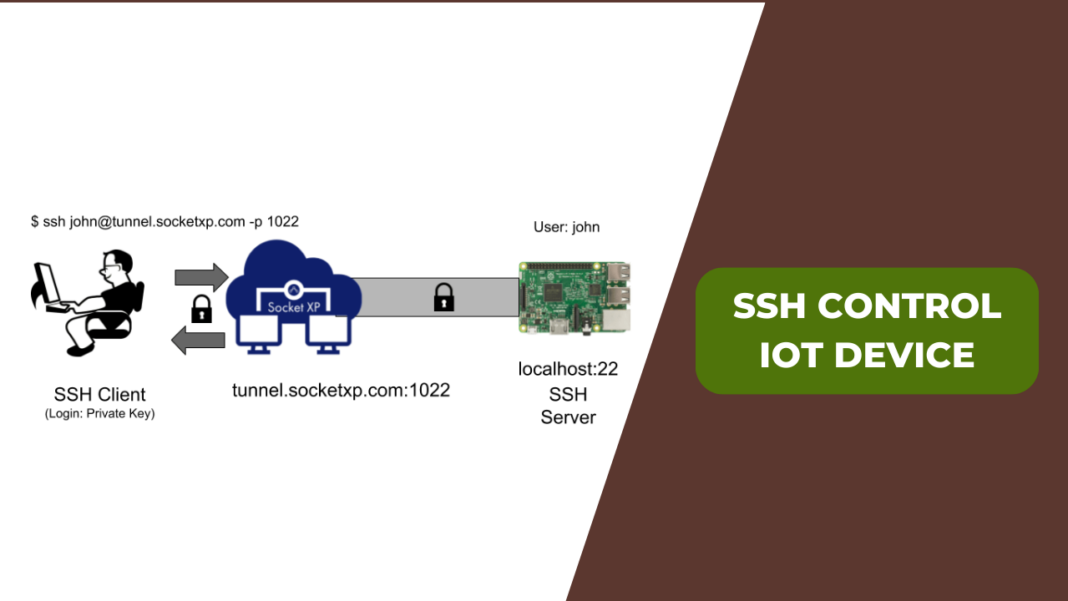
SSH remote IoT device management refers to the practice of controlling and monitoring Internet of Things devices from a remote location using Secure Shell (SSH). This method provides a secure and encrypted connection, ensuring data integrity and confidentiality while allowing administrators to perform essential tasks without physical access to the device.
With SSH, users can execute commands, transfer files, and configure settings on IoT devices from anywhere in the world. This capability is particularly valuable for organizations managing large-scale IoT deployments, where physical access to every device is impractical.
The increasing reliance on IoT devices in industries such as healthcare, manufacturing, and smart homes has elevated the importance of secure remote management. SSH plays a critical role in this ecosystem, offering a reliable solution for maintaining and optimizing IoT networks.
What is SSH?
Secure Shell (SSH) is a cryptographic network protocol designed to provide secure communication over an unsecured network. It enables users to remotely access and manage devices while protecting sensitive data through encryption.
How SSH Works
SSH operates by establishing a secure channel between a client and a server. The protocol uses public-key cryptography to authenticate users and encrypt data, ensuring that only authorized individuals can access the system. Once the connection is established, users can execute commands, transfer files, and perform other administrative tasks securely.
Key Features of SSH
- Encryption: SSH encrypts all data transmitted between the client and server, preventing unauthorized access.
- Authentication: SSH supports various authentication methods, including passwords, public keys, and certificates, to verify user identity.
- Port Forwarding: SSH allows users to securely forward traffic from one network to another, enabling remote access to services behind firewalls.
Benefits of Using SSH for IoT Devices
Utilizing SSH for IoT device management offers numerous advantages, making it a preferred choice for professionals and organizations alike. Below are some of the key benefits:
Read also:Surya Mcgregor The Rising Star In Martial Arts And Beyond
- Enhanced Security: SSH encrypts all communication, protecting sensitive data from interception and unauthorized access.
- Remote Access: Administrators can manage IoT devices from anywhere in the world, improving efficiency and reducing the need for physical presence.
- Automation: SSH enables the automation of repetitive tasks, such as backups and updates, saving time and reducing errors.
- Scalability: SSH can handle large-scale IoT deployments, ensuring consistent performance across numerous devices.
By leveraging SSH, organizations can ensure the security and reliability of their IoT networks while maintaining operational efficiency.
Setting Up SSH for IoT Devices
Setting up SSH for IoT devices involves several steps, including enabling the SSH service, configuring security settings, and testing the connection. Below is a step-by-step guide to help you get started:
Enabling SSH on IoT Devices
Most modern IoT devices come with SSH pre-installed, but it may need to be enabled manually. Here's how to enable SSH on common IoT platforms:
- Raspberry Pi: Enable SSH by navigating to the Raspberry Pi Configuration tool and selecting the SSH option.
- Arduino: Install an SSH server on the device using a compatible operating system, such as Ubuntu Core.
Configuring Security Settings
Once SSH is enabled, it's crucial to configure security settings to protect your device from unauthorized access. This includes:
- Changing the default password to a strong, unique one.
- Disabling root login to prevent direct access by administrative accounts.
- Using public-key authentication instead of passwords for added security.
Securing Your SSH Connections
While SSH provides a secure method for remote access, additional measures can further enhance its security. Below are some best practices for securing SSH connections:
Use Strong Passwords and Public Keys
Strong passwords and public-key authentication are essential for preventing unauthorized access. Public keys provide an additional layer of security by requiring a unique key pair for each user.
Limit Access to Specific IPs
Restricting SSH access to specific IP addresses can reduce the risk of brute-force attacks. This can be achieved by configuring firewall rules or using tools like fail2ban.
Monitor Logs for Suspicious Activity
Regularly reviewing SSH logs can help identify potential security threats. Look for unusual login attempts or failed authentication requests that may indicate malicious activity.
Managing IoT Devices Remotely with SSH
Once SSH is set up and secured, you can begin managing your IoT devices remotely. Below are some common tasks you can perform using SSH:
Executing Commands
SSH allows you to execute commands directly on the IoT device, enabling you to perform tasks such as checking system status, updating software, and restarting services.
Transferring Files
Using SSH, you can securely transfer files between your local machine and the IoT device. This is particularly useful for deploying firmware updates or transferring configuration files.
Monitoring System Performance
SSH provides access to system monitoring tools, allowing you to track resource usage, network activity, and other performance metrics in real-time.
Troubleshooting Common SSH Issues
Despite its reliability, SSH can occasionally encounter issues that may affect its functionality. Below are some common problems and their solutions:
Connection Refused
If you receive a "connection refused" error, ensure that the SSH service is running on the IoT device and that the correct IP address and port number are being used.
Authentication Failed
Authentication failures can occur due to incorrect passwords, mismatched public keys, or disabled authentication methods. Verify your credentials and ensure that the correct authentication method is enabled.
Timeout Errors
Timeout errors may indicate network issues or excessive latency. Check your network connection and consider increasing the SSH timeout settings if necessary.
Best Practices for SSH Remote IoT Device Management
To ensure optimal performance and security when managing IoT devices remotely with SSH, follow these best practices:
- Regularly update the SSH server and client software to address security vulnerabilities.
- Implement multi-factor authentication (MFA) for added security.
- Document all SSH configurations and procedures for future reference.
By adhering to these guidelines, you can maximize the benefits of SSH while minimizing potential risks.
Applications of SSH in IoT
SSH has a wide range of applications in the IoT ecosystem, including:
Network Management
SSH enables administrators to configure and monitor IoT networks remotely, ensuring optimal performance and security.
Device Configuration
With SSH, users can configure IoT devices without physical access, streamlining deployment and maintenance processes.
Data Collection
SSH facilitates the secure transfer of data between IoT devices and central servers, enabling real-time analysis and decision-making.
The Future of SSH in IoT
As the IoT landscape continues to evolve, SSH will remain a critical tool for secure remote management. Advances in encryption technologies and the growing adoption of quantum-resistant algorithms will further enhance its capabilities, ensuring its relevance in the years to come.
Additionally, the integration of SSH with emerging technologies such as blockchain and artificial intelligence (AI) may lead to new and innovative applications in IoT management.
Conclusion
SSH remote IoT device management is a powerful and secure solution for controlling and monitoring IoT devices from anywhere in the world. By following the guidelines outlined in this article, you can effectively set up, secure, and manage your IoT devices using SSH.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and related technologies. Together, let's build a safer and more connected future!